Tech Scam Survival Guide
Hey there! Have you ever received a suspicious email or phone call claiming to be from tech support, warning you about viruses on your computer or offering to fix issues you didn’t even know existed? Well, you’re not alone. Tech scams have become increasingly prevalent in today’s digital age, with scammers employing various tactics to trick unsuspecting individuals into divulging sensitive information or paying for unnecessary services. Let’s take a closer look at some of the most common tech scammer trends you should watch out for.
One notorious trend is the “tech support” scam, where scammers impersonate reputable companies like Microsoft or Apple and reach out to users via phone calls or pop-up messages. They claim that your computer has been infected with a virus or malware and offer to fix the problem remotely for a fee. In reality, they may install harmful software or gain access to your personal data.
Another common tactic is phishing emails, where scammers pose as legitimate organizations, such as banks or online retailers, and request sensitive information like passwords or credit card numbers. These emails often contain urgent messages, urging recipients to click on malicious links or download attachments that install malware on their devices.
Additionally, fake antivirus software scams prey on users’ fear of malware infections by displaying alarming pop-up messages claiming to have detected viruses on their devices. The scammers then prompt victims to purchase fake antivirus software or services to remove the nonexistent threats. Lastly, there’s the “ransomware” scam, where malware encrypts the victim’s files and demands payment in exchange for the decryption key. Scammers may disguise ransomware as legitimate software downloads or attachments, tricking users into inadvertently infecting their devices.
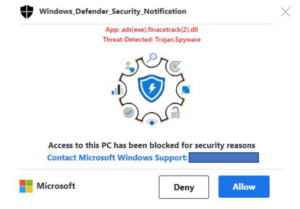
Have you seen something like this on your computer?
To protect yourself from falling victim to these scams, it’s essential to stay vigilant and skeptical of unsolicited communications, especially those requesting sensitive information or payment. Always verify the legitimacy of the sender or caller by contacting the company directly through official channels. Additionally, keep your software and security tools up to date, and regularly back up your data to mitigate the impact of potential attacks.
In conclusion, while tech scams continue to evolve, awareness and caution remain your best defenses against falling prey to these malicious schemes. By staying informed and adopting proactive security measures, you can safeguard yourself against the ever-present threat of tech scammers. Stay safe out there!
This month, Murph Consulting turned 18. I cranked up Alice Cooper's "I'm 18" and Skid Row's "18 and Life" to get the vibes going. My company is now old enough to vote, get a tattoo, and get married, all without parental consent. Watch out, world!
In all seriousness, the passing of another year of entrepreneurship and running a successful business always feels like a good time to reflect. Since we started in 2007, we've assisted nearly 600 small businesses and residential clients. Businesses in every industry, ranging in size from the solopreneur to 100 employees. There’s no company we’ll say “you’re too small for us to help”, and that gives me great joy. Small businesses need tech and CyberSecurity support, and we’ve got their backs.
Speaking of, it's October again, and you all know what that means, right? The Mets have failed us, and the Islanders, Jets, and Rangers are about to. It's also Cybersecurity Awareness Month. Every small business should be implementing some basic security measures by now. It's easier and more affordable than you think it is, and definitely cheaper than dealing with the fallout of something drastically bad happening to your business.
How's your password game? Do you use strong passwords on all the sites you visit, or are they all slight modifications of one word, like your kids or pets' names or birth dates?
If it's the latter, let's chat. You should be using a password manager. They are easy to use, create complex passwords for you that you no longer need to remember, and keep them all safe for you. I can't remember the last time I had to click on the "forgot your password" link for any site, and I love that for me.
A password manager is just one of the seven software we feel EVERY small business should have in place to help keep them protected in 2025. We’ve packaged these up together neatly and made them affordable for the small businesses we will always support. If you’d like to learn more, please click the “Contact Murph” button below to send me an email.